Is India Cyber proof?
By MYBRANDBOOK

Cyberattacks are now recognised as the fifth dimension in warfare after air, water, land and space. India is among the top three countries in the world after the US and China when it comes to phishing and malware attacks. Is India prepared for cyberattacks?
Phishing is one of the most common types of cyberattacks, mainly because it is an effective technique for gaining access to an organization’s network and systems. As a common practice we always expect the Government to secure everything for us and our enterprises against any kind of attacks, which is not true on the basis of reality. Countries such as India, Australia and Japan are facing increasingly sophisticated attacks on government agencies and organizations providing critical infrastructure services.
A survey gauged the priorities, difficulties and progress of their implementations of new cyber defense technologies such as cloud cybersecurity modernization, endpoint detection and response and extended detection and response (EDR-XDR), multifactor authentication (MFA) and zero trust architecture (ZTA).
Thirty-two percent of Indian respondents claim to have fully implemented cloud cybersecurity modernization and 29% appear to have fully implemented multifactor authentication (MFA). The cyber defense technologies lagging furthest behind in India appear to be zero trust architectures (25% at full deployment) and EDR-XDR (22% at full deployment).
Fifty-nine percent of Indians surveyed believe their government could provide more funding to organizations such as theirs to improve cybersecurity. Fifty-three percent favour tighter cooperation on the investigation of attacks following their discovery, and 44% favoured tighter cooperation on cyber incident management while attacks are in progress. Forty-seven percent favour improved guidance on best practices, and 46% favoured a combination of incident notification and liability protection to facilitate sharing of attack data between impacted organizations, government partners and industry audiences. Forty-one percent of respondents support greater consequences for malicious actors when caught, and 35% support more regulations of a yet to be determined nature.
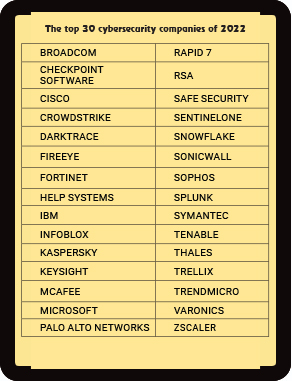 While cybersecurity is vital for all industries, there is a maximum scope of growth in sectors that have witnessed rapid transformation on the back of digital disruption. Fast-growing sectors such as BFSI, education and healthcare must have robust cybersecurity systems to secure their data and operations.
While cybersecurity is vital for all industries, there is a maximum scope of growth in sectors that have witnessed rapid transformation on the back of digital disruption. Fast-growing sectors such as BFSI, education and healthcare must have robust cybersecurity systems to secure their data and operations.
According to business and consumer data company Statista, in the financial year 2021, over 3.8 thousand government services in India were provided over the internet. A report from CLSA indicates the value of digital payments in India will grow three-fold – close to 1 trillion dollars in FY26 from 300 billion dollars in FY21.
A Deloitte study has said, India will have 1 billion smartphone users by 2026. The country was home to 1.2 billion mobile subscribers in 2021, of which about 750 million were smartphone users. As on January 2021, India had 448 million social media users. In 2021, the DBS Digital Readiness survey revealed almost 62 percent of large and middle-market companies are still in the formative stages of digitalisation in India.
These are big numbers, and point to the vastness of the cyberspace that India needs to secure. The country is also a witness to numerous cyberattacks in the past, including many soft ones. The government’s ongoing Digital India push and the Reserve Bank’s planned Central Bank Digital Currency may only add to the list of vulnerabilities.
As per the report, India was expected to be among the largest victims of cyberattacks in two years. Cyberattacks were projected to increase by 200 per cent year-on-year.
According to the Computer Emergency Response Team data, India witnessed a three-fold increase in cybersecurity-related incidents in 2020 compared to 2019, recording 1.16 million breaches. The number of breaches is expected to increase in 2021 and 2022. According to government sources, there has been 6,07,220 recorded cybersecurity breaches till June 2021.
In 2021-22, the government outspend its budgeted estimates on cyber security for the first time in past eight years. In this year’s budget, the government said it would spend 515 crore rupees on cyber security in 2022-23.That’s a 10 times increase, compared to 2014-15.
Presently, the nature of the war in Ukraine indicates that India needs to review its cyber-defence policies. The country also needs to give equal attention to building a deterrent cyber-offensive capability. The government is taking far too long in finalising a National Cyber Security Strategy.
Therefore, any new strategy must ensure the private sector has necessary cyber-security cover. The new strategy must also acknowledge that the capacity to counter-attack is often the best defence in a cyber-war.
Protect yourself against cyberattacks
One can avoid cyber risks by taking steps in advance:

During a cyberattack
After a cyberattack
Cyber Crime Emergency Response Team (CERT) is India’s 1st crime investigation agency who look after for cybercrime related cases, digital evidence collection, create new investigation method to solve organized crime, solve high profile crime cases.
 Cyber CERT is providing support to government officials, agencies, investigation firms.
Cyber CERT is providing support to government officials, agencies, investigation firms.
Change, Compliance, Cost, Continuity, and Coverage; these are all fundamental considerations for an organization. For anyone challenged with evaluating and implementing technical solutions, these factors provide a useful lens through which to assess available options. With the past as our guide it is clear that the future will demand more flexibility, reach, and capacity more quickly and at lower costs. The Internet has already changed the way we live, learn, and communicate with each other. It is also changing the nature of software and how we interact with it. We are moving from static applications purchased in boxes to living cyber platforms shared with thousands of users, adopted as needed and discarded if not valued.
SaaS changes our relationship with software by allowing us to focus on what it does for us—not the infrastructure required to make it work. This change allows businesses to invest more in their people and in differentiating technologies and less on non-strategic functions.
SaaS also changes our relationships with software providers by creating a mutually dependant environment in which the seller of the service is fully committed to the customer’s long-term outcomes. No one expects a customer to continue to pay for a solution that is not providing value to their organization. The Software as a Service model creates a vendor-vested relationship from the very start and places the consumer in a more powerful position. If your organization would benefit from rapid access to state-of-the-art technology delivered with minimal internal resource requirements, tremendous scalability, and predictable costs over time, then your organization should consider a SaaS based option for your physical security needs.
Organized cybercrime groups are often run like multinational corporations. They are profit-motivated and therefore seek to structure themselves, innovate, grow, and operate in certain respects the way a competitive private sector company would. The degree of organization in cybercrime networks varies, but working together allows cybercriminals to pool complementary skills, which can lead to greater success and economic gain over time.
Organized cybercrime groups often pursue multiple crime types, diversifying their fraud activities to increase the groups reach and profit. As organized cybercrime groups have evolved from romance scams to business email compromise (BEC), for example, many have added new tools and techniques to their operations, rather than replacing past scams with the latest. Large organized cybercrime groups typically have healthy budgets, due to the large profit margins in cybercrime, and are renowned early adopters of new technology and tactics, techniques, and procedures (TTPs).

Consequently, organized cybercrime groups have the means to invest significant sums of money into technology. Early technology adoption and large budgets allow cybercrime groups to take advantage of advanced technology faster than law enforcement, which is constrained by government budgets and procurement cycles.
Protection against cybercrime
 Cybercriminals orchestrate malware, ransomware, phishing, DDoS attacks, identity theft, etc. to steal valuable data or money. Fortunately, we can adapt best practices to protect ourselves from malicious actors. The first line of defence is using antivirus and other security solutions that provide us visibility at Wire-speed. Updating operating system and software, using strong passwords, not opening attachments in the spam mailbox, refraining from accessing or giving out personal data on untrusted websites and keeping a strict vigil on bank statements can protect us.
Cybercriminals orchestrate malware, ransomware, phishing, DDoS attacks, identity theft, etc. to steal valuable data or money. Fortunately, we can adapt best practices to protect ourselves from malicious actors. The first line of defence is using antivirus and other security solutions that provide us visibility at Wire-speed. Updating operating system and software, using strong passwords, not opening attachments in the spam mailbox, refraining from accessing or giving out personal data on untrusted websites and keeping a strict vigil on bank statements can protect us.
Solutions to prevent distributed dos attacks (ddos)
There are different techniques used to mitigate DDoS such as having distributed assets in the network which will reduce the attack surface, Rate limiting technique which will limit the number of requests a server will accept over a time period from a particular IP, having Web Application Firewall (WAF), adding rules to your gateway infrastructure which accepts traffic from a legitimate source.
One of the effective ways to mitigate DDoS attacks for enterprise application servers is hiding from malicious users. It can be achieved by using Zero Trust Access for enterprise applications that use drop-all firewall rules in your gateway infrastructure. It drops all the traffic which doesn’t come from legitimate devices. A fundamental principle here is “A hacker can’t attack what it cannot detect”.
Approach to the current situation
Traditional approaches can no longer be adopted to tackle these sophisticated cyberattacks. Malicious actors need to be dealt with using state-of-the-art security solutions that use Artificial Intelligence and Machine Learning to create cyber situational awareness. NDR solutions need to be deployed to ensure network visibility in real-time and network forensics should be performed to analyse the loopholes.
Role of AI/ML in cybersecurity processes?
Artificial intelligence and machine learning have provided new capabilities to detect and resolve security incidents. AI provides insights that can help businesses identify a potential threat quickly and reduce response time. It can process a massive amount of data and use reasoning to determine suspicious addresses and files. AI can also help in securing user authentication and determine if a user is authorised to access a technology device.
Machine learning recognises patterns in data to help machines learn from experience. A key benefit of machine learning is that it detects and responds to an issue almost immediately. Thus, it prevents potential threats from disrupting business operations and makes it faster and easier to counter threats. With the help of machine learning, AI can learn patterns quickly and process huge volumes of unstructured information to provide insights with higher efficiency.
Many cybercrimes are facilitated by cryptocurrency, which - when not regulated closely - can enable cybercriminals to transfer and cash out (withdraw cryptocurrency into cash) illicit funds anonymously. Consequently, Indian lawmakers are considering passing a bill  that could greatly influence cybercriminal operations in India- the law would completely ban private cryptocurrencies such as Bitcoin. The bill would criminalize any possession, mining, or trading of cryptocurrencies and violators would be subject to fines. If India implements this law, it could have a dampening effect on cybercrime activity in the country because many cybercrime operations rely on cryptocurrency to fund their activities.
that could greatly influence cybercriminal operations in India- the law would completely ban private cryptocurrencies such as Bitcoin. The bill would criminalize any possession, mining, or trading of cryptocurrencies and violators would be subject to fines. If India implements this law, it could have a dampening effect on cybercrime activity in the country because many cybercrime operations rely on cryptocurrency to fund their activities.
Additionally, India is a favourable environment for cybercriminals given the combination of minimal public awareness of cybersecurity issues as well as vulnerabilities in India’s cybersecurity infrastructure. India’s consumers, businesses, and policymakers are not well-versed in cybersecurity, which makes them easy targets for cybercriminals, especially when there are few cybersecurity mechanisms in place to safeguard internet users.


Legal Battle Over IT Act Intensifies Amid Musk’s India Plans
The outcome of the legal dispute between X Corp and the Indian government c...

Wipro inks 10-year deal with Phoenix Group's ReAssure UK worth
The agreement, executed through Wipro and its 100% subsidiary,...

Centre announces that DPDP Rules nearing Finalisation by April
The government seeks to refine the rules for robust data protection, ensuri...

Home Ministry cracks down on PoS agents in digital arrest scam
Digital arrest scams are a growing cybercrime where victims are coerced or ...


Icons Of India : AALOK KUMAR
Aalok Kumar is celebrated as a global leader and recipient of the Peop...

Icons Of India : NEERAJ MITTAL
He started his career as an IAS Officer in 1992. He has held various a...

Icons Of India : Arundhati Bhattacharya
Arundhati Bhattacharya serves as the Chairperson and CEO of Salesforce...


TCIL - Telecommunications Consultants India Limited
TCIL is a government-owned engineering and consultancy company...

EESL - Energy Efficiency Services Limited
EESL is uniquely positioned in India’s energy sector to address ener...
CERT-IN - Indian Computer Emergency Response Team
CERT-In is a national nodal agency for responding to computer security...


Indian Tech Talent Excelling The Tech World - Vinod Dham, Founder & Executive Managing Partner, IndoUS Venture Partners
Vinod Dham, known as the “Father of the Pentium Chip,” has left an...

Indian Tech Talent Excelling The Tech World - Dheeraj Pandey, CEO, DevRev
Dheeraj Pandey, Co-founder and CEO at DevRev , has a remarkable journe...

Indian Tech Talent Excelling The Tech World - JAYASHREE ULLAL, President and CEO - Arista Network
Jayshree V. Ullal is a British-American billionaire businesswoman, ser...
 of images belongs to the respective copyright holders
of images belongs to the respective copyright holders