AI-driven attacks are a concerning trend in the cyber security landscape
By MYBRANDBOOK

Cybersecurity is a complex and ever-evolving field. There is no silver bullet that will completely protect us from cyberattacks. Cybersecurity has become a critical concern for businesses, governments, and individuals alike. As India embraces rapid digitization, its citizens, businesses, and government sectors reap substantial benefits. However, this digital revolution brings forth significant cybersecurity challenges at the same time.
The rise of cloud computing, AI, ML, Gen AI and increasing usage of mobile and mobility devices has further expanded the attack surface, making it more challenging to secure digital assets and data. Businesses today are at risk from cybersecurity threats that are increasing in both variety and sophistication, such as social engineering attacks, ransomware, various forms of malware, and Distributed Denial of Service (DDoS) attacks. An alarming development in the cyber threat landscape is the rise of AI-driven attacks.
Cyberattacks are on the rise across sectors and the attacks have become more sophisticated. Recently, healthcare organizations have increasingly being targeted. AI is still a relatively new technology in cybersecurity, but it has the potential to revolutionize the field. By automating tasks and improving threat detection and response, AI can help organizations to protect themselves from increasingly sophisticated attacks.
The cybersecurity market in India is projected to reach significant revenue milestones in the coming years. By 2024, the market is expected to achieve a revenue of approximately USD 4.70 billion and is anticipated to grow at a compound annual growth rate (CAGR) of 18.33%, reaching about USD 10.90 billion by 2029. This robust growth is driven by the increasing demand for digitalization, the adoption of scalable IT infrastructure, and the need to address various cybersecurity risks
By 2024, the market in India is expected to achieve a revenue of approximately USD 4.70 billion and is expected to reach to USD 10.90 billion by 2029.
We can’t deny the fact that, AI-driven attacks different from traditional cyber attacks. AI-driven attacks use artificial intelligence (AI) and machine learning algorithms to study and adapt to an organization’s cybersecurity defenses, making them more sophisticated and difficult to detect than traditional cyber attacks. They can quickly analyze vast amounts of data to identify vulnerabilities and exploit them, often in real-time, without the need for human intervention.
One of the key differences between AI-driven attacks and traditional cyber attacks is their speed and scale. AI-driven attacks can launch multiple malicious tasks simultaneously, overwhelm defenses, and cause widespread damage in a short amount of time.
Additionally, AI can develop strategies to outsmart traditional defense mechanisms and constantly evolve their tactics to stay ahead of security measures. The adaptive nature of AI-driven attacks also presents a challenge for traditional cybersecurity experts. These attacks can constantly learn and adapt, making it difficult to predict their behavior and defend against them effectively. This constant evolution requires cybersecurity experts to continually update and improve their defenses, as well as to develop new strategies to combat rapidly changing threats.
Overall, the sophistication, speed, and adaptability of AI-driven attacks make them more concerning for cybersecurity experts, as they pose a significant threat to organizations and their data. To combat these threats effectively, cybersecurity experts must have the knowledge and resources to stay ahead of evolving cyber threats and employ advanced security measures that can effectively detect and respond to AI-driven attacks.
Cyber security experts are particularly concerned about AI-driven attacks because of their ability to outpace and outsmart traditional defense mechanisms. These attacks are constantly evolving and becoming more sophisticated, making it increasingly challenging for defenders to keep up.
Additionally, the widespread availability of AI tools and technologies means that even novice attackers can leverage these capabilities to launch advanced and highly effective cyber attacks. As a result, cyber security experts must continually innovate and adapt their defenses to combat the growing threat posed by AI-driven attacks
The importance of cybersecurity cannot be overstated in today’s digital landscape. As organizations increasingly rely on technology to conduct their operations, the risks associated with cyber threats have become more pronounced.
The common tactics used in AI-driven attacks are.
Adversarial machine learning: Attackers can manipulate or trick AI algorithms by feeding them malicious data in order to bypass security measures. Organizations can defend against this by regularly updating and testing their AI models with a diverse range of data, implementing anomaly detection techniques, and using multiple algorithms in combination for added security.
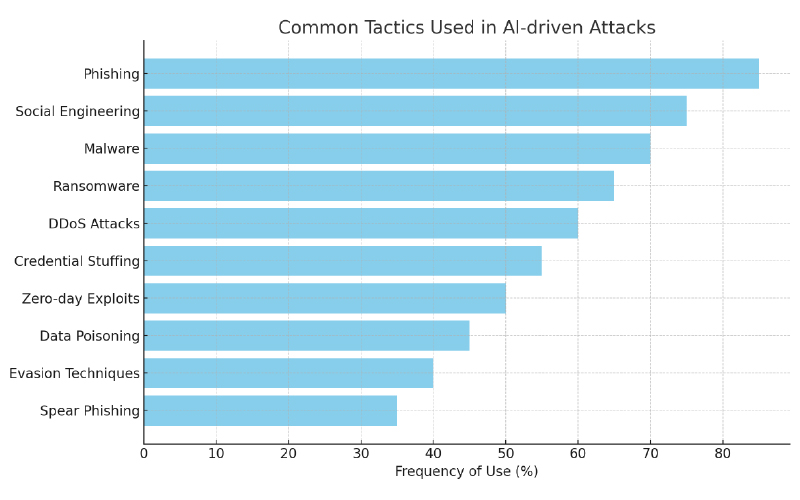
Data poisoning: Attackers can inject false or misleading data into AI systems to manipulate outcomes. Organizations can defend against this by implementing data validation and verification processes, monitoring data sources for unusual patterns, and using encryption to protect sensitive data.
Model inversion: Attackers can reverse-engineer AI models to extract sensitive information or intellectual property. Organizations can defend against this by implementing security measures such as access controls, encryption, and regularly auditing and updating their AI models.
Model stealing: Attackers can steal AI models and use them for malicious purposes. Organizations can defend against this by implementing strong authentication and access controls, monitoring for unauthorized access, and encrypting sensitive data.
Denial-of-service attacks: Attackers can overload AI systems with a high volume of requests, causing them to crash or become unresponsive. Organizations can defend against this by implementing rate limiting, monitoring system performance, and using distributed denial-of-service (DDoS) protection mechanisms.
It is high time to integrate AI and machine learning in cyber security tools and strategies help to detect and prevent AI-driven attacks more effectively.
Advanced threat detection: AI and machine learning algorithms can analyze vast amounts of data in real-time to identify patterns and anomalies that may indicate an AI-driven attack. By continuously learning and adapting, these tools can stay ahead of evolving threats and detect them before they cause harm.
Behavior analysis: AI can be used to analyze user behavior and detect unusual patterns that may indicate an AI-driven attack. Machine learning algorithms can identify deviations from normal behavior and flag them for further investigation, helping to prevent unauthorized access or data breaches.
Automated response: AI-powered cyber security tools can automate the response to potential threats, allowing for faster and more effective mitigation of attacks. These tools can automatically block suspicious activity, isolate infected systems, and take other defensive actions to prevent AI-driven attacks from spreading.
Predictive capabilities: Machine learning algorithms can analyze historical data to predict future threats and vulnerabilities, allowing organizations to proactively strengthen their defenses and minimize the potential impact of AI-driven attacks. By understanding the tactics and techniques used by attackers, organizations can stay one step ahead and prevent future breaches.
Enhanced threat intelligence: AI can be used to analyze threat intelligence feeds and identify emerging trends and patterns in cyber attacks. By aggregating and analyzing large volumes of data from various sources, AI-powered tools can provide organizations with actionable insights to improve their cyber security posture and prevent AI-driven attacks.
Organizations can defend against AI-driven attacks by implementing a multi-layered security approach, regularly updating and testing AI systems, and monitoring for suspicious activities. Collaboration between security professionals, data scientists, and AI developers is also crucial to effectively defend against evolving threats.
The digitization drive across industry segments is exposing traditional industries such as automobiles, manufacturing, healthcare to cyber threats.
Biggest challenges for Indian businesses into cyber security and cyber crime
The CISO (Chief Information Security Officer) typically holds a senior leadership position within a company’s executive team. They are responsible for overseeing the organisation’s information security strategy, ensuring compliance with regulations, and protecting data from cyber threats. The constant evolution of cyber threats, including advanced persistent threats (APTs), zero-day vulnerabilities, and sophisticated malware, makes it challenging to stay ahead of attackers. CISOs must continuously monitor and adapt to these changes.

The Chief Information Security Officer (CISO) plays a crucial role in ensuring the security of an organization’s information and technology infrastructure. Their responsibilities include developing and implementing cybersecurity policies and procedures, overseeing the organization’s security operations, and managing the response to cybersecurity incidents. The CISO’s role has a significant impact on an organization’s overall cybersecurity strategy and effectiveness in several ways:
Leadership and Governance: The CISO provides strategic leadership and guidance on cybersecurity matters, ensuring that the organization’s security program aligns with its business objectives and regulatory requirements. They develop and implement governance structures that help prioritize security initiatives and allocate resources effectively.
Risk Management: The CISO is responsible for identifying and assessing cybersecurity risks, developing risk mitigation strategies, and monitoring the effectiveness of controls. By understanding the organization’s risk profile, the CISO can help ensure that security measures are targeted at protecting the most critical assets and data.
Incident Response: The CISO plays a key role in coordinating the organization’s response to cybersecurity incidents, including breaches, malware attacks, and other security incidents. They ensure that the organization has defined incident response processes in place, conducts regular incident response drills, and responds promptly and effectively to any security incidents.
Security Technology and Tools: The CISO evaluates, procures, and implements security technologies and tools to protect the organization’s systems and data. They stay abreast of the latest security trends and technologies to ensure that the organization’s security capabilities remain current and effective. 5. Security
Awareness and Training: The CISO is responsible for developing and implementing security awareness and training programs to educate employees about cybersecurity risks and best practices. By promoting a security-aware culture within the organization, the CISO can help reduce the likelihood of security incidents caused by human error.
The CISO’s role is critical in shaping an organization’s cybersecurity strategy and ensuring its effectiveness. By providing strategic leadership, managing risks, coordinating incident response efforts, implementing security technologies, and promoting security awareness, the CISO helps protect the organization’s information assets and mitigate cybersecurity threats effectively.
One of the biggest challenges that Indian businesses are facing is data overload. The migration to cloud and accelerated digital transformation, especially after the pandemic has led to data proliferation. As a result, cloud security monitoring has become difficult and basic security controls have become redundant as sophisticated attacks are increasing. In a cloud-based environment, where there are innumerable endpoints and users, there are concerns regarding data loss and data leakage, data privacy, lack of visibility of who can access the data, vulnerabilities in cloud based applications, compliance requirements, account hijacking, etc.
Fact sheets:
Cost of Cybercrime: The global cost of cybercrime is projected to reach $10.5 trillion annually by 2025, reflecting a significant increase from previous years.
Ransomware: The average cost of a ransomware attack has risen to $4.54 million, with recovery costs excluding ransom payments averaging $1.82 million. Despite paying the ransom, only 8% of businesses recovered all their data.
Phishing: Phishing remains the most common email attack method, accounting for 39.6% of all email threats. Approximately 94% of malware is delivered via email.
Cloud Intrusions: There has been a 75% increase in cloud intrusions, with attackers using legitimate credentials to access cloud environments, making it difficult to distinguish between normal user activity and a breach.
Business Interruption: Cyber incidents are the most feared cause of business interruption, surpassing natural disasters. Spending on information security and risk management is expected to grow by 14.3% in 2024, reaching over $215 billion.
Cyber attacks in India continue to grow
Key- Takeaways:
As India advances its digitalization efforts across sectors, a pervasive outbreak of cyberattacks has inflicted substantial financial losses on businesses. Cybersecurity has ascended to a strategic concern at the board level owing to the multifaceted nature of cyber threats and the escalating monetary repercussions stemming from data breaches.
The number of new malware threats is truly staggering. A estimates suggest that around 560,000 new pieces of malware are discovered every single day. That’s a lot of malicious software constantly being created. These daily discoveries add up, with over 1 billion malware programs already circulating in the digital world. This vast number makes it challenging to stay completely secure.
Artificial intelligence is rapidly becoming a key component of cybersecurity. AI is the most disruptive technologies of our time. AI can be used to automate tasks, identify threats, and respond to incidents more quickly and effectively than humans can.
Role of AI in cybersecurity is to anticipate potential vulnerabilities and future attacks via predictive analytics, while automated threat hunting reduces the workload on cybersecurity professionals by identifying threats within a network. AI uses predictive analytics to anticipate potential vulnerabilities and future attacks. Machine learning models analyze historical data, threat patterns, and network behavior to predict where and how future attacks might occur. By identifying potential threats before they materialize, organizations can implement proactive measures to fortify their defenses.
Additionally, AI indeed plays a transformative role in Identity and Access Management (IAM) systems and enhances overall cybersecurity efforts. AI continuously monitors user activities to establish a baseline of normal behavior. It detects anomalies by comparing current actions against this baseline, identifying potential unauthorized access or misuse. AI dynamically adjusts access controls based on real-time risk assessments. If a user’s behavior deviates from the norm, AI can trigger additional authentication steps or restrict access to sensitive resources.
Finally:
As we progress to the mid of 2024, the landscape of cybersecurity in India and the APAC region presents a complex mix of challenges and evolving threats. The adoption of advanced technologies like AI and ML, the increasing importance of cloud security, and the ever-present human factor, all underline the need for robust, proactive cybersecurity strategies. Organizations must stay ahead of these trends and continuously evolve their cybersecurity posture to safeguard their assets and maintain the trust of their stakeholders.
The Top 30 Cybersecurity Companies In India
| ACRONIS | CROWDSTRIKE | FORTINET | MANAGEENGINE | SENTINELONE | THALES |
| BROADCOM | ETEK | IBM | MANDIANT | SNOWFLAKE | TRELLIX |
| CHECK POINT | FIREEYE | INFOBLOX | MICROSOFT | SONICWALL | TREND MICRO |
| CISCO | FORCEPOINT | KASPERSKY | PALO ALTO | SOPHOS | VARONIS |
| CLOUDFLARE | FORESCOUT | KEYSIGHT | RSA | TENABLE | ZSCALER |


Legal Battle Over IT Act Intensifies Amid Musk’s India Plans
The outcome of the legal dispute between X Corp and the Indian government c...

Wipro inks 10-year deal with Phoenix Group's ReAssure UK worth
The agreement, executed through Wipro and its 100% subsidiary,...

Centre announces that DPDP Rules nearing Finalisation by April
The government seeks to refine the rules for robust data protection, ensuri...

Home Ministry cracks down on PoS agents in digital arrest scam
Digital arrest scams are a growing cybercrime where victims are coerced or ...


Icons Of India : Arundhati Bhattacharya
Arundhati Bhattacharya serves as the Chairperson and CEO of Salesforce...

ICONS OF INDIA : SRIDHAR VEMBU
Sridhar Vembu is the chief executive officer (CEO) of Zoho Corporation...

ICONS OF INDIA : SUNIL BHARTI MITTAL
Sunil Bharti Mittal is the Founder and Chairman of Bharti Enterprises,...


GSTN - Goods and Services Tax Network
GSTN provides shared IT infrastructure and service to both central and...

IOCL - Indian Oil Corporation Ltd.
IOCL is India’s largest oil refining and marketing company ...

IREDA - Indian Renewable Energy Development Agency Limited
IREDA is a specialized financial institution in India that facilitates...


Indian Tech Talent Excelling The Tech World - Anirudh Devgan , President, Cadence Design
Anirudh Devgan, the Global President and CEO of Cadence Design Systems...

Indian Tech Talent Excelling The Tech World - Sundar Pichai, CEO- Alphabet Inc.
Sundar Pichai, the CEO of Google and its parent company Alphabet Inc.,...

Indian Tech Talent Excelling The Tech World - ARVIND KRISHNA, CEO – IBM
Arvind Krishna, an Indian-American business executive, serves as the C...
 of images belongs to the respective copyright holders
of images belongs to the respective copyright holders