Hackers are exploiting a platform-agnostic flaw to track mobile phone locations
By MYBRANDBOOK
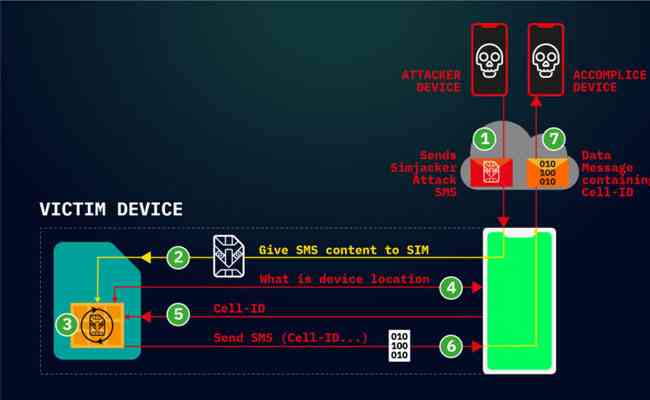
Hackers are actively exploiting a critical weakness found in most mobile phones to surreptitiously track the location of users and possibly carry out other nefarious actions, researchers warned. Attacks work by sending commands directly to applications stored on SIM cards.
The Simjacker exploits work across a wide range of mobile devices, regardless of the hardware or software they rely on, researchers with telecom security firm AdaptiveMobile Security said in a post. The attacks work by exploiting an interface intended to be used solely by cell carriers so they can communicate directly with the SIM cards inside subscribers’ phones. The carriers can use the interface to provide specialized services such as using the data stored on the SIM to provide account balances.
Simjacker abuses the interface by sending commands that track the location and obtain the IMEI identification code of phones. They might also cause phones to make calls, send text messages, or perform a range of other commands.
Dan Guido, a mobile security expert and the CEO of security firm Trail of Bits, told Ars the threat looked “pretty fucking bad.” He added: “This attack is platform-agnostic, affects nearly every phone, and there is little anyone except your cell carrier can do about it.”
Over the past two years, AdaptiveMobile Security researchers said, they have observed devices from “nearly every manufacturer being successfully targeted to retrieve location.” Device makers include Apple, ZTE, Motorola, Samsung, Google, Huawei, and even those who produce Internet-of-things products that contain SIM cards. While basic attacks work on virtually all devices, more advanced variations-such as making a call-would work only on specific phones that don’t require users to confirm they want the call to go through.
This attack is also unique, in that the Simjacker Attack Message could logically be classified as carrying a complete malware payload, specifically spyware. This is because it contains a list of instructions that the SIM card is to execute. As software is essentially a list of instructions, and malware is “bad” software, then this could make the Simjacker exploit the first real-life case of malware (specifically spyware) sent within a SMS. Previous malware sent by SMS-such as the incidents we profiled here-have involved sending links to malware, not the malware itself within a complete message.
The researchers said other commands UICCs are capable of executing include:
PLAY TONE
SEND SHORT MESSAGE
SET UP CALL
SEND USSD
SEND SS
PROVIDE LOCAL INFORMATION (including location, battery, network, and language)
POWER OFF CARD
RUN AT COMMAND
SEND DTMF COMMAND
LAUNCH BROWSER
OPEN CHANNEL (CS BEARER, DATA SERVICE BEARER, LOCAL BEARER, UICC SERVER MODE, etc.)
SEND DATA
GET SERVICE INFORMATION
SUBMIT MULTIMEDIA MESSAGE
GEOGRAPHICAL LOCATION REQUEST
The attack reported ,there is similar to one demonstrated in 2013 at the Black Hat security conference in Las Vegas.
“We could trigger the attack only on SIM cards with weak or non-existent signature algorithms, which happened to be many SIM cards at the time,” Karsten Nohl, the chief scientist at SRLabs who presented the 2013 findings, told Ars. “AdaptiveMobile seems to have found a way in which the same attack works even if signatures are properly checked, which is a big step forward in attack research.”
Nohl added that he doubted Simjacker was being widely exploited, since location data is generally not interesting to criminals and other methods exist to track specific targets. Those methods include SS7 attacks, phone malware, or simply buying the data from mobile networks or app makers who collect it.
In response to the attacks, the SIMalliance-an industry group representing major UUIC makers-issued a new set of security guidelines for cellular carriers. The recommendations include:
* Implementing filtering at the network level to intercept and block “illegitimate binary SMS messages” and
* Making changes to the security settings of SIM cards issued to subscribers.
As Nohl noted, snoops have long had a variety of ways to track the location of many cellular devices. Thursday’s report means that, until carriers implement the SIMalliance recommendations, hackers have another stealthy technique that previously went overlooked.


Nazara and ONDC set to transform in-game monetization with ‘
Nazara Technologies has teamed up with the Open Network for Digital Comme...

Jio Platforms and NICSI to offer cloud services to government
In a collaborative initiative, the National Informatics Centre Services In...

BSNL awards ₹5,000 Cr Project to RVNL-Led Consortium
A syndicate led by Rail Vikas Nigam Limited (abbreviated as RVNL), along wi...

Pinterest tracks users without consent, alleges complaint
A recent complaint alleges that Pinterest, the popular image-sharing platf...


ICONS OF INDIA : ROSHNI NADAR MALHOTRA
Roshni Nadar Malhotra is the Chairperson of HCLTech, a leading global ...

Icons Of India : NATARAJAN CHANDRASEKARAN
Natarajan Chandrasekaran (Chandra) is the Chairman of Tata Sons, the h...

Icons Of India : Debjani Ghosh
Debjani Ghosh is the President of the National Association of Software...


NPCI - National Payments Corporation of India
NPCI is an umbrella organization for operating retail payments and set...

IFFCO - Indian Farmers Fertiliser Cooperative
IFFCO operates as a cooperative society owned and controlled by its fa...

UIDAI - Unique Identification Authority of India
UIDAI and the Aadhaar system represent a significant milestone in Indi...


Indian Tech Talent Excelling The Tech World - Vinod Dham, Founder & Executive Managing Partner, IndoUS Venture Partners
Vinod Dham, known as the “Father of the Pentium Chip,” has left an...

Indian Tech Talent Excelling The Tech World - George Kurian, CEO, Netapp
George Kurian, the CEO of global data storage and management services ...

Indian Tech Talent Excelling The Tech World - Shantanu Narayen, CEO- Adobe Systems Incorporated
Shantanu Narayen, CEO of Adobe Systems Incorporated, is renowned for h...