CYBER SECURITY
By MYBRANDBOOK
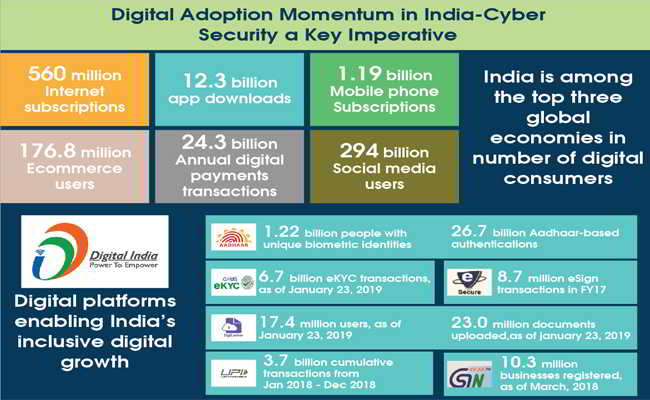
Digital India initiatives bring various disruptive technologies as opportunity for the technology players, who understand the value of data, which they say is the new oil.
The cybersecurity market in India is growing exponentially and is expected to employ over a million professionals by 2025. With 15% of enterprises having experienced a targeted attack and more than 53% losing sensitive data as a result, India’s need for cybersecurity has never been more vital. The attacks are becoming more and more sophisticated, with phishing, identity thefts, advanced worms, DOS and DDOS all attacking vulnerable users who aren’t equipped to deal with them.
The last decade has seen an exponential growth in cyber-crimes. At one hand technology has made common life simpler, but it has also given rise to crimes designed and devised by technology. Traditional crimes are today replaced with modern crimes, wherein the computer is used as a tool to attack common people and victimize them.
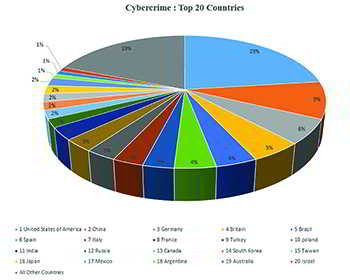 The issues concerning cyber-crime investigation is more complex and requires an analytical mind blended with technology and legal ramifications. Traditional crimes did not have much jurisdictional issues, whereas cybercrime has a bigger role related to jurisdictional issues. A criminal sitting in different continent can attack a digital device in other continent and hence the investigation becomes more complex in collecting and seizing of electronic evidence. The complexity arises to a new bar when the legal proceedings start.
The issues concerning cyber-crime investigation is more complex and requires an analytical mind blended with technology and legal ramifications. Traditional crimes did not have much jurisdictional issues, whereas cybercrime has a bigger role related to jurisdictional issues. A criminal sitting in different continent can attack a digital device in other continent and hence the investigation becomes more complex in collecting and seizing of electronic evidence. The complexity arises to a new bar when the legal proceedings start.
The provisions in Information Technology Act 2000 has laid various provisions and sections leading to a fair trial. The last amendment of the IT ACT 2000 was done in 2008. Technology in the past 11 years has gone to a new level, but the law has not yet been modified to cater to modern crimes and hence may lead to acquittal of many cases where in electronic evidence could not be established against the accused. This is a serious concern and hence law enforcement and the judicial system has to work together to ensure that the criminals are booked and convicted according to the provisions in the law.
Cyberattack is one of the important security challenges that the country is facing today or the world is facing. The cyberattacks can pose wide-ranging threats to power grids; they can impact and cripple financial institutions that can result in leakage of sensitive information and so on. A report shows that more than fifty per cent of cybercrimes in India are traced back to this sleepy town of Jharkhand.
Home Secretary Rajiv Gauba said more than half of India’s crimes committed by fraudsters posing as bank managers were traced back to Jamtara.
With the fact that digitization happening at a faster speed, there is a requirement to build safeguards for protecting and preserving vital company data. Jamtara is recognised as the Cybercrime capital of India. Cyberattacks have become more organised with significant funding, passion, they have become sophisticated, they often gain access and they wait for the right time, for the moment of their choice for their attacks.
It was the era of IT – vulnerabilities on the Network, Operating Systems, the applications, the virtual environments, Mobile Devices and Mobile Applications. Now the bad boys are moving their action into OT, where we are seeing the Industrial malware evolving to become autonomous, extensible, and capable of executing device commands specific to a particular ICS environment - Smart cars. Smart security cameras. Smart medical implants.
Everything around us is always connected and communicating, swapping data with other devices and uploading it to the global internet to help automobile, home, factory, business, and body perform better. It’s no wonder that 15 billion connected things will be in use till 2019, supported with the rise of social media and e-commerce.
As we are entering into the technology disruption phase with the emergence of IoT technology, consumer apps have been transformed to highly complex level manufacturing and industrial applications. IoT is expected to transform business results for different industries. It is all about improving employee efficiency, creating new digital offerings, delivering new products, and creating an ecosystem that strengthens holistic solutions. Many industries have already identified IoT devices as clear value differentiators for their businesses.

The cause of growth
The most highlighted terminologies including digitization, automation, AI, cloud, social media, blockchain, IoT and other such disruptive technologies are progressing at an enormous pace, totally exposing the data and other critical resources of an organization. The required security measures to safeguard and protect such vital resources have not developed at the same pace.
Challenges in cybersecurity
Lack of skilled cyber security professionals, want of security culture in organisations, voluminous data and absence of loyalty in employees are some of the key challenges faced today.
Need of the hour for the country to think
Digital India initiatives bring various disruptive technologies as opportunity for the technology players, who understand the value of data, which they say is the new oil. At the same time, the country has also been named as the most cybercrime vulnerable country in the world.
The RBI has recently reported that each working day banks are reporting over 5000 cyber security breaches each single day. The highly technologically developed and robust Aadhaar IT system was recently hacked by a young systems coder for the sake of fun and entertainment. Another instance is that the large GST tech system has also been exposed to severe cyber security breaches.
All this shows that India is a very fertile country for growing cybercrimes. With more and more banking and other such systems migrating to the cloud, it will create a more fertile ground for such cybercrimes.
Enhancing cyber security strategy
Cyber security has to be built into the information security system as an ongoing proactive measure. There should be a team of cyber security experts that should constantly monitor, ethically hack and validate the integrity of the IT systems. All cyber accesses and operations must be closely monitored on an ongoing basis. Our suggestion will also be to document and administer a strong protocol and supervision driven system that constantly monitors employee access to the IT systems.
There is a strong recommendation for involving the HR management to monitor and evaluate behavioural patterns of employees working in the IT area for preventive identification of such criminal acts. It is an opportunity for the educational institutions to come up with the specialised course on Cybersecurity for achieving the long term and sustainable goal.
Finally, IoT, Big Data, and AI are all fed into each other and this creates an ecosystem of automation - IoT devices collect data on millions of criteria and use to train and improve AI algorithms and many do not know how these technologies are linked. As such, people should understand how IoT, Big Data and AI interact with each other to bring real improvements in business processes and improve their lifestyle.
Be Prepared!!!
Cyber-attacks are evolving from the perspective of what they target, how it affects the organizations, and evolving methodologies of attack. Information theft is the most expensive and fastest rising consequence of cyber crime. However, data is not the only target. Core systems such as industrial controls are being hacked in a dangerous trend to disrupt and destroy.
While data remains a key target, theft is not always the outcome of an attack. A new wave of cyber attacks sees data no longer just being copied but being destroyed or changed, in attempts to breed distrust. Attacking data integrity is the next frontier of cyber threats.
Cyber criminals are adapting various attack methods, such as they are aiming at the human layer. They are the weakest link in cyber defense, through increased ransomware and phishing and social engineering attacks as a path to entry.
"


InterGlobe’s Rahul Bhatia and C.P. Gurnani together announce
In a move that is set to transform the AI landscape, Rahul Bhatia, Group M...

Download masked Aadhaar to improve privacy
Download a masked Aadhaar from UIDAI to improve privacy. Select masking w...

Sterlite Technologies' Rs 145 crore claim against BSNL rejecte
An arbitrator has rejected broadband technology company Sterlite Technolog...

ID-REDACT® ensures full compliance with the DPDP Act for Indi
Data Safeguard India Pvt Ltd, a wholly-owned subsidiary of Data Safeguard ...


Technology Icons Of India 2023: Rajiv Memani
As Chair of the EY Global Emerging Markets Committee, Rajiv connects e...

Technology Icons Of India 2023: Lt Gen (Dr.) Rajesh Pant (Retd.)
LT Gen(Dr.) Rajesh Panth (Retd.), National cyber security coordination...

Technology Icons Of India 2023: Girish Mathrubootham
Girsh Mathrubootham envisioned and co-founded Freshworks. Freshworks, ...


BEL leveraging next generation technologies to keep the country ahead in Defence space
Bharat Electronics Limited (BEL) is a Navratna PSU under the Ministry ...

Aadhaar: Architecting the World's Largest Biometric Identity System
The Unique Identification Authority of India (UIDAI) is a statutory au...

PGCIL transforming India with its wide power transmission network
Engaged in power transmission, POWERGRID or PGCIL is a stated owned In...


EXCLUSIVE NETWORKS SALES INDIA PVT. LTD.
Exclusive Networks is a globally trusted cybersecurity specialist hel...

SONATA INFORMATION TECHNOLOGY LIMITED
Sonata Software Limited is a leading Modernization engineering company...

WPG C&C COMPUTERS & PERIPHERALS PVT. LTD.
WPG C&C Computers & Peripherals (India) was incorporated in 2008 and ...